Spotlights
Information Security Officer, Computer Security Specialist, Data Security Administrator, Network Security Analyst
Information security analysts protect an organization’s computer systems and digital files by planning and enforcing security measures. This involves regular monitoring of networks and investigating a breach of security, should one occur.
AI agents can detect threats faster than ever, but cybercriminals are also using AI tools. Cybersecurity professionals must adapt by overseeing AI-driven defenses, anticipating emerging risks, and developing strategic security frameworks.
- Being able to help people with complex problems they may not understand, but at the end of the day makes them more secure
- Intellectually challenging tasks and different challenges everyday create an interesting work environment
- Get to be on the front lines of new exploits/security problems, and developing solutions to fix them
Communication: checking email to review issues people have reported and determine if a client needs help, if there is a host compromised or if there is a security emergency which needs to be addressed
- Examples of reported issues are if a system was compromised with regular malware, or a researcher left information on a laptop which is lost/stolen.
- Information security analysts must also document detected breaches of security in reports submitted to management
Consulting: information security analysts also serve subject matter experts.
- For example, if a computer user wants to start a service online but wants to be secure about it, or if they want to install and use an online security product, an information security analyst can guide them
- Information security analysts also recommend security measures or software to management
Addressing technical challenges: performing system administration work
- Setting up firewalls and data encryption programs to protect data and information
- Detect security breaches and determine their root cause
- Testing the current system for vulnerabilities by simulating attacks
- Building new security tools for the information security office
- Enhancing existing tools through configuration changes
Researching: staying up to date on new security tools and/or products
-
Although information security analysts address these tasks throughout the day, they face different people and challenges on a day-to-day basis
Soft Skills
- Critical thinking and problem-solving
- Analytical and detail-oriented
- Speaking and active listening
Technical Skills
- Security penetration and vulnerability testing
- Knowledge of anti-virus and anti-malware programs
- Computer electronics: networking, routing and switching, knowledge of circuit boards, processors
- Firewall and intrusion detection/prevention protocols
- Programming languages: C, C++, C#, Java or PHP
- Cloud computing
- Security Information and Event Management (SIEM)
Software Skills
- Operating systems: e.g. Microsoft Windows, Bash, UNIX, and Linux
- Web development: e.g. JavaScript, AJAX, Microsoft ASP.NET
- Network monitoring and security: e.g. Nagios, Wireshark, Intrusion Prevention System, Websense Data Loss Prevention
- Virtually any organization that uses computers will at some point need an Information Security Analyst to make sure their systems run securely
- Information security is especially critical to hospitals and government offices
- At the entry-level, information security analysts can expect to work long hours
- Information security analysts may also be put on call, when they will be required to have their phone on them 24/7 so they can be first-responders in the event of a security breach (which may occur at odd hours)
- A variety of information security certificates make you a stronger candidate for a position as an information security analyst
- Students are now starting to learn programming languages as early as possible, to give them an edge of the competition and also because there is just so much to lear
- Puzzles
- Reading
- Any activity which requires curiosity and a passion for tinkering!
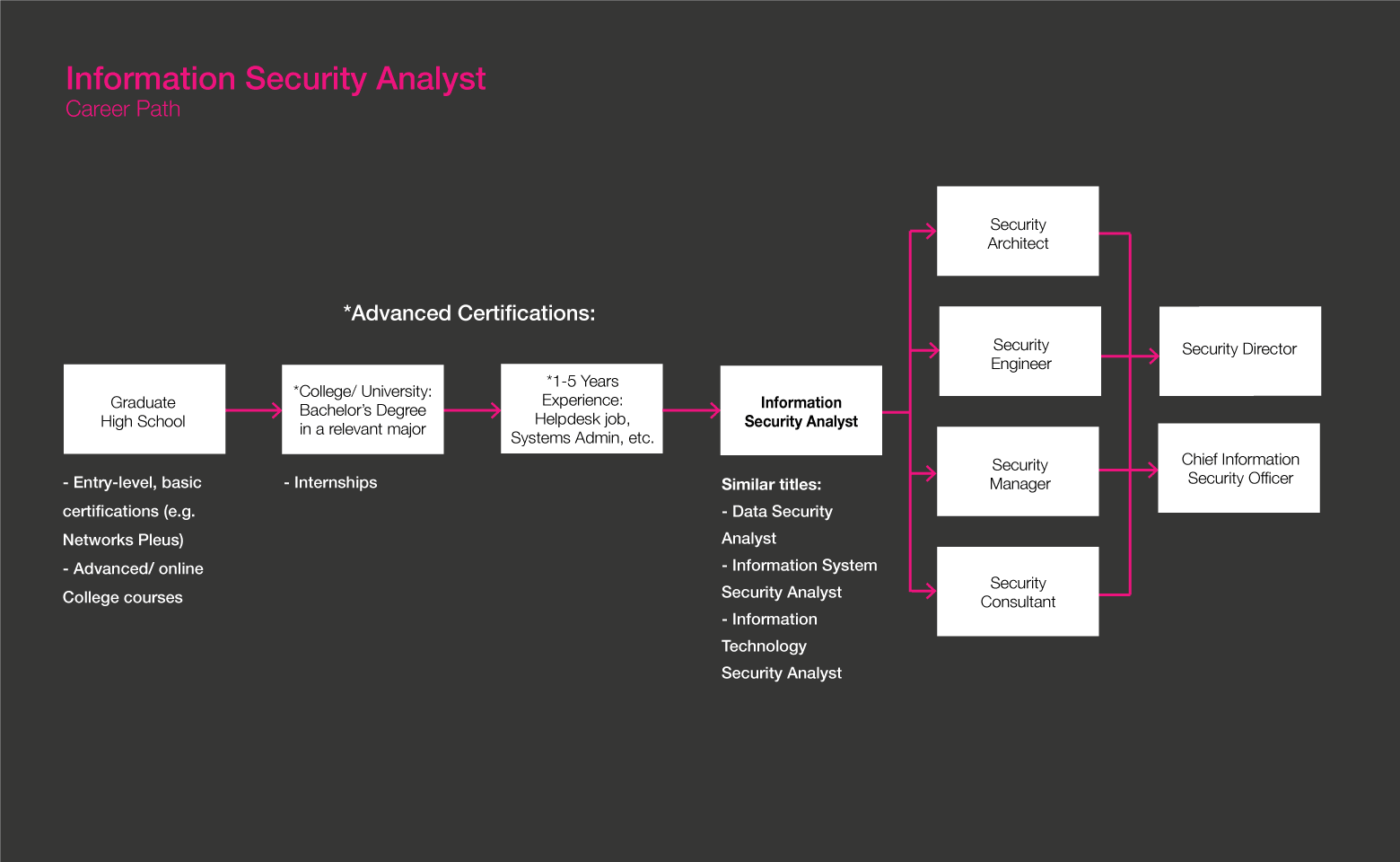
- Information Security Analysts can get started with a bachelor’s in computer science, cybersecurity, or other computer and information technology major. In some cases, sufficient work experience and certifications are enough to land an entry-level position
- There are dozens of Information Security Analyst-related certificates available, including:
- Amazon - AWS Certified Security Specialty
- American Health Information Management Association - Certified in Healthcare Privacy and Security
- Broadcom:
- Administration of Symantec Cloud Workload Protection
- Administration of Data Center Security
- CIW:
- CIW Web Security Associate
- CIW Web Security Professional
- Cisco:
- Cisco Certified CyberOps Associate
- CCIE Security Certification
- CompTIA:
- Security+
- CompTIA Advanced Security Practitioner
- CompTIA CDIA+
- Cybersecurity Analyst
- Cloud Credential Council - Cloud Technology Associate+ Certification
- Conference of State Bank Supervisors - Certified Information Systems Examiner
- Dell Corporation - Specialist - Infrastructure Security
- EC-Council:
- Certified Incident Handler
- Certified Chief Information Security Officer
- Certified Threat Intelligence Analyst
- ETA International - Electronic Security Networking Technician
- Information Technology Security ETA International
- (ISC)2 - Certified Information Systems Security Professional
- Federal IT Security Institute - FITSP-Manager
- Global Information Assurance Certification:
- Global Industrial Cyber Security Professional
- GIAC Critical Controls Certification
- GIAC Cyber Threat Intelligence
- GIAC Defensible Security Architecture
- GIAC Assessing and Auditing Wireless Networks
- Google - Professional Cloud Security Engineer
- HP - HP ASE - ArcSight Logger V1
- IBM - IBM Certified Analyst - i2 Analysts Notebook V9
- Information Systems Audit and Control Association:
- Certification in Risk and Information Systems Control
- Certified Information Systems Auditor
- CSX Cybersecurity Practitioner
- Microsoft - Certified Azure Security Engineer Associate
- Oracle - Cloud Platform Identity and Security Management 2021 Certified Specialist
- Popular programming languages for Information Security Analysts are Java, JavaScript, Python, SQL, PHP, PowerShell, and C
- Some universities offer a specialized bachelor’s degree in Information Security or Cyber Security. This is a useful option if you are sure about going into the information security field.
- Some universities’ information security degree syllabi only feature theoretical teachings. Programs which offer hands-on training in information security (such as penetration tasks, learning security tools or learning attack techniques) prepare students to be stronger candidates in the job market.
Universities with acclaimed information technology programs (for further research):
- Utica College
- University of California- Berkeley
- Syracuse University
- Champlain College
- Arizona State University
- Harvard VPAL/Harvard X
- http://www.edfoundation.org/
- https://www.afcea.org/site/foundation/scholarships/stem-majors
- https://scholars.horatioalger.org/scholarships/about-our-scholarship-programs/
- https://careers.microsoft.com/students/scholarships
- http://nshssfoundation.org/scholarships/stem-scholarships/
- http://www.dodstem.us/stem-programs/scholarships
- https://research.adobe.com/
- https://www.roboticseducation.org/competition-teams/scholarships/
- https://www.ieee.org/education_careers/education/preuniversity/scholarship.htm
- Start reading about computers, information technology, programming concepts as early as possible
- Watch YouTube videos and tutorials about Information Security concepts and skills
- Participate in relevant internships if they are available, or co-ops as they become available (it is important to get as much hands-on/on the job experience as you can)
- Take a college course early (while in high schools), or get a certification to show academic interest in a formal education in Information Security
- If you get into programming or coding, build a portfolio demonstrating tools you can use
- Create blog about Information Security news or tools (you may feature your portfolio on this blog)
- At an advanced level, you may be able to start writing information security tools yourself. This should be posted on your blog to increase your marketability
- Take plenty of computer-related classes to prepare for tough college courses
- Decide if you want to pursue a bachelor’s or not; O*Net notes that 53% of Information Security Analysts have a bachelor’s, 23% have a post-bacc certificate, and 13% hold an associate’s
- Work on the certifications needed for the jobs you’re interested in
- Join computer clubs, learn new skills, and gain real-world practice
- Watch video tutorials, read books and blogs, and participate in discussion forums
- Apply to Information Security Analyst intern jobs to gain real-world experience
- Take online courses to learn applicable programming languages like Python
- Create a knowledge base where you can keep and share notes with peers
- Draft a working resume that you can add to as you complete academic and work experiences
- Information Security Analyst jobs are projected to grow 33% in the coming decade, meaning there should be lots of opportunities
- Having the right certifications is essential. The Bureau of Labor Statistics notes that workers will be especially needed for cloud services adoption and in banks, corporations, and the healthcare industry
- Ask your school’s career center for help with resume writing, mock interviews, job fair info, and ways to connect with recruiters
- Notice which states do the most hiring! Virginia, Texas, Florida, New York, and Maryland have the highest employment rates for this field
- Ask references in advance before giving out their contact information on application materials
- Build profiles on job portals such as Monster, Indeed, Glassdoor, Zippia, Machine Hack, MLconf Job Board, Y Combinator, Stack Overflow, AngelList, and DataJobs. Don’t forget to use LinkedIn, too!
- Apply to jobs you’re best qualified for through a mix of academics and hands-on experience
- Pay attention to the keywords used in job ads, and incorporate them into your resume
- Check out Information Security Analyst resume templates for ideas
- Prep for interviews by reading Information Security Analyst interview questions
- Having a passion and curiosity for continual learning
- An affinity for solving puzzles and breaking down complex problems
- Ability to work efficiently in a high-pressure environment and under tight deadlines
Websites
- ISC2
- Association for Computing Machinery
- CompTIA
- Computing Research Association
- High Technology Crime Investigation Association
- IEEE Computer Society
- Information Systems Security Association
- InfraGard
- National Center for Women & Information Technology
Books
- An information security analyst will possess the experience and skills to transition into almost any Computer Science related field (e.g. computer networking, systems administration, information management)
- Information security analysts may also transition into the privacy field, which is distinct from information security, but goes hand-in-hand with it (e.g. sometimes larger organizations employ a privacy officer)
Newsfeed

Featured Jobs

Online Courses and Tools








